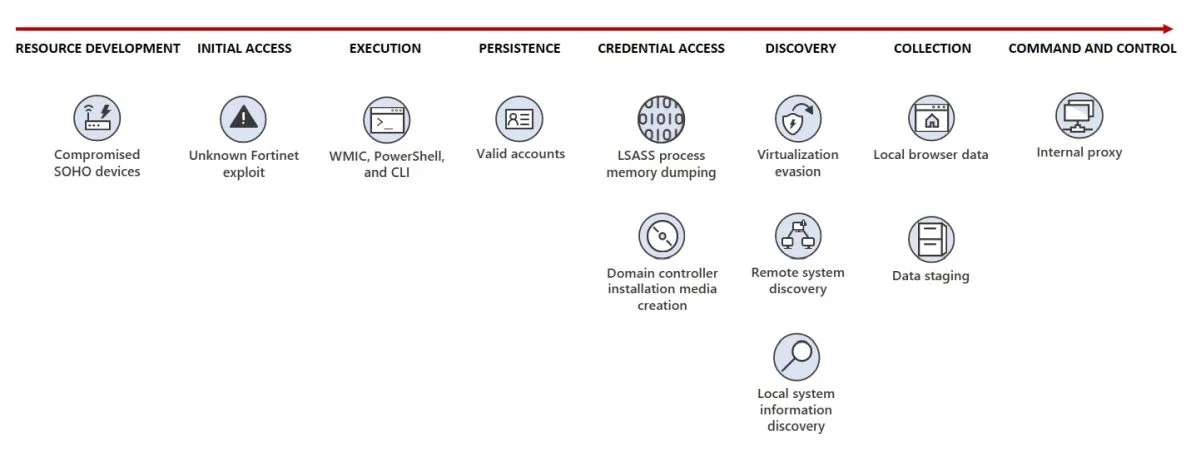
As written in Microsoft’s blog, Volt Typhoon has targeted critical infrastructure organizations in Guam – one of the US’ most crucial military outpost, Andersen airbase, is located on the island – and elsewhere in the US. In its current campaign, the targeted organisations span the communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors. Further, observed behavior suggests that the hacker group intends to perform espionage and maintain access without being detected for as long as possible. “Volt Typhoon proxies all its network traffic to its targets through compromised SOHO network edge devices (including routers). Microsoft has confirmed that many of the devices, which include those manufactured by ASUS, Cisco, D-Link, NETGEAR, and Zyxel, allow the owner to expose HTTP or SSH management interfaces to the internet. Owners of network edge devices should ensure that management interfaces are not exposed to the public internet in order to reduce their attack surface. By proxying through these devices, Volt Typhoon enhances the stealth of their operations and lowers overhead costs for acquiring infrastructure.” It’s not Microsoft that is sounding alarms about Volt Typhoon either. The Five Eyes Intelligence network, which comprises the US, Australia, Canada, New Zealand, and the UK, also released a statement that outright fingered China and the threat actor in its state-sponsored hacking activities. “The United States and international cybersecurity authorities are issuing this joint Cybersecurity Advisory (CSA) to highlight a recently discovered cluster of activity of interest associated with a People’s Republic of China (PRC) state-sponsored cyber actor, also known as Volt Typhoon.”
On that note, China hasn’t brushed off these allegations but has lambasted the allegations that it is sponsoring Volt Typhoon, saying that the collective “lacked evidence” and that the US, specifically, is “expanding channels for disseminating false information”. Having said that, it is not wrong to say that China is an old hand at being accused of hacking and brushing off accusations, even when the evidence is stacked against the country. (Source: Microsoft, ,Tech Monitor, JCA)